E-mail is increasingly losing its reliability as a way for businesses to send
notifications to interested consumers, according to new figures from a
message-monitoring firm.
Unsolicited bulk e-mail (UBE, also known as spam) has grown so rapidly that it
now outnumbers legitimate e-mail 4-to-1. Internet service providers, in
an attempt to avoid spam complaints from end users, routinely block millions of messages
every day. As a result, a large percentage of legitimate business notifications,
which users voluntarily signed up to receive, never arrive. One ISP
currently rejects more than half of such notifications, a consulting firm says.
Pivotal Veracity, a service that works under contract for several Fortune 1000
corporations, is in the business of measuring the number of e-mail messages that
actually get through to their intended recipients.
The Arizona-based firm, which was founded in 2003, monitors only "permission-based" or "opt-in" e-mail lists, according to the firm's president, Deirdre
Baird. That means the recipients of the messages must have signed up to receive
communications via e-mail. Corporations that "rent" e-mail addresses aren't
accepted into the monitoring program, says Baird, much less outright spammers.
The messages that are being monitored include newsletters, notices of sales,
transaction confirmations, and other business-based communications.
Unfortunately, the legitimate nature of these messages is no guarantee they'll
be delivered as intended.
ISPs Are On The Defensive
Many Internet service providers advertise that they protect their users from
spam. That may be true, and it's certainly a worthy goal. But millions of
e-mails that these ISPs automatically delete appear to be messages that the
intended recipients asked for.
Three ISPs -- Excite, NetZero and Verizon -- currently delete or bounce more than one-quarter of
the opt-in messages that Pivotal Veracity's clients send to opt-in recipients,
according to figures provided by Michelle Eichner, the firm's vice president of
client services.
Even when an e-mail message avoids outright deletion, it can be misrouted by an
ISP into a folder labeled "spam," "junk" or "bulk." Consumers rarely examine
these folders to catch errors. Three ISPs -- Hotmail, Yahoo and Google Mail --
presently misroute more than one-eighth of requested e-mail into such folders,
according to Pivotal Veracity's figures.
Now You See It, Now You Don't
To monitor e-mail deliverability, the consulting firm obtains numerous e-mail
accounts at various ISPs. These include business-to-consumer ISPs, such as AOL,
Comcast and Earthlink, and enterprise-oriented filtering services, such as
BrightMail, MessageLabs and Postini. When an ISP maintains two separate lines
of business (such as Yahoo and its partner, SBC), they are treated separately in
the figures.
During the period from March 15 to April 15, the monitored ISPs deleted,
bounced
or misrouted the following percentage of its clients' opt-in e-mails, according
to the firm's figures (in descending order of deleted/bounced opt-in e-mails):
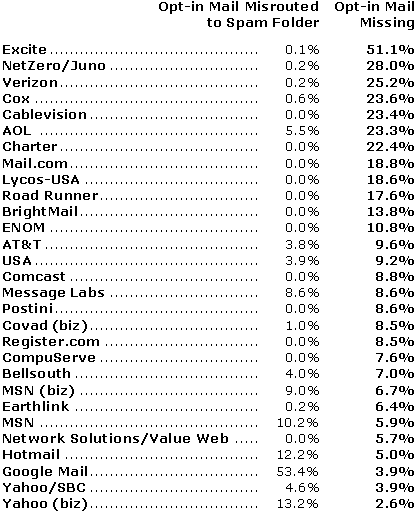
Some ISPs that rejected a fairly low number of permission-based e-mails had a
high rate of shunting requested e-mails into a "spam" folder. Google Mail's
gmail.com service, which is in beta-test mode at the present time, was the worst
in this regard, according to Eichner, mislabeling more than 53% of
permission-based messages as spam.
Overall, permission-based messages are being misrouted to spam folders 7% of the
time, and rejected 15% of the time, according to industrywide averages
published by Pivotal Veracity.
It's true that the consulting firm's clients may be sending e-mails that contain
"spammy" words, such as "sale" and "discount." But it's also true that real
people signed up for these notifications because they were interested in the
subject matter. These customers may not even be aware that their ISPs aren't
delivering to their inboxes the messages they requested.
Affirmative Measures for Legitimate Senders
Personally, I no longer allow companies I do business with to send me
notifications and billing information via e-mail. I require that I receive
important notices via postal mail. If a company sends me a bill using postal
mail, I figure there's a 99% chance I'll actually receive it.
That's a terrible commentary on how lousy we've allowed e-mail delivery to
become.
Companies that want to improve the percentage of permission-based messages that
their opt-in subscribers receive do have a few steps they can take, says Baird:
• Verify your HTML content. Minor errors in the HTML coding of
e-mail messages can have a big effect. Baird says ISPs often summarily delete
messages that contain such errors, since spammers often use malformed HTML to
evade filters. Before sending an HTML communication, you can catch coding errors
by running your file through the free W3C validation service.
• Apply for membership in ISP whitelists. Internet service
providers commonly maintain lists of high-volume e-mail publishers who are not
spammers. Each ISP has its own peculiar way that you must apply for membership,
but once you've completed the process it can pay big dividends in improved
deliverability.
• Monitor block lists. One of the biggest surprises that's emerged
in her studies, Baird says, is the severe penalty that's applied by some ISPs to
messages that contain links to "banned" Web addresses. A single such link can
result in 100% of your messages being rejected by AOL, Cablevision, Charter,
Hotmail and MSN, according to Pivotal Veracity. To check whether a link in a
planned mailing is forbidden, you can pre-send the message to test accounts
you've obtained at various ISPs or do this using a commercial service such as
Baird's.
Conclusion
To demonstrate the seriousness of the threat to e-mail as a communications
medium, Baird says her firm is planning to release next month the results of an
extensive test. In this experiment, Pivotal Veracity subscribed to the e-mail
lists of more than 100 major corporations. When signing up, her firm used the
e-mail addresses of scores of test accounts maintained at more than 25 ISPs.
Every corporate mailing was then monitored to see which messages arrived safely,
which were mislabled as spam, and which were deleted entirely by an ISP.
Baird says the results will shock some corporations that believed e-mail was a
reliable way to reach customers. "37% of those companies had one or more of
their e-mails placed in the spam or bulk folder," she states. "That includes
U.S. FDA drug alerts and messages from the Wall Street Journal, AARP, Walgreen,
Wal-Mart, SAS, and IBM."
When her new study is published in May, it will be made available free of
charge, Baird says. You can look for word of its release at PivotalVeracity.com.



